How Blockchain Maintains Information Validity and Security
The basic approach to blockchain security
A blockchain consists of a network of digital ledgers distributed between users (each user has a copy of the same ledger). Users can engage in peer-to-peer (P2P) transactions, which reduces the time and cost of traditional transactions where an intermediary, such as a bank, is involved. However, without some sort of recognised central authority, what is to stop unscrupulous users from engaging in dishonest behaviour, such as selling the same good to more than one person or altering the records on the ledger? The structure of a blockchain is designed to prevent such behaviour:
- Transactions are validated by a consensus of users. Although we use the term ‘users’ here, the validation process is an algorithmic process conducted by the computers of the participants in the network (and later, as we get into a more technical description, we shall adopt the term ‘nodes’ in order to better reflect this).
- Users compete to add valid blocks of new transactions to the blockchain.
- Attempting to add a new block of transactions incurs a computational cost for a user, but this is offset by the reward that is received if the block is accepted by the other users.
- Security is ensured through a combination of cryptographic protocols and unique identifiers attached to messages (known as “hash values”).
- Users have two keys: a public key, which identifies them; and a private key, used for digitally signing transactions.
- A transaction consists of the sender’s public key, the recipient’s public key, and information pertaining to what is being transacted (e.g. currency).
- To sign a transaction, the sender receives the hash value of the transaction and signs this hash value with their private key (using a signature algorithm) to produce a digital signature.
- Any user can verify a transaction (using a verify algorithm) by using the sender’s public key and the hash value of the transaction.
- A hacked or corrupted transaction will produce a different hash value, which recipients will detect once they attempt to verify the transaction with the digital signature.
- A hacker would have to hack all ledgers in the network simultaneously, which is virtually impossible.
- A system of referencing within and between blocks means that any attempt at tampering would break the connections within the chain, and so be detected.
Achieving consensus
Rather than relying on a central authority to validate transactions, a transaction is validated by a consensus of users. Some blockchains require that a transaction is approved by at least 51% of users, but others set a higher threshold for approval.
Hash functions
Once a transaction has been added to the blockchain, it cannot be altered. The protection of records in the blockchain is ensured by a branch of cryptography known as ‘hash functions’.
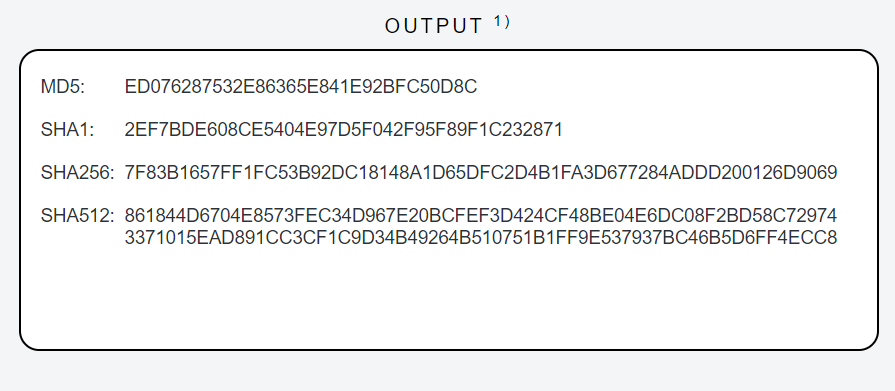
A hash function is an algorithm that takes any kind of input and transforms it into a unique fixed-length string of digits and letters. This string is known as the ‘hash value’. The function is one-way, such that the original data cannot be discovered from the hash value. There are many different hash functions that produce strings of different lengths. The example in Figure 1 shows four different hash function outputs for the text “Hello World!”. See for yourself by typing this text into the hash function tool, which is associated with Daniel Drescher’s fine demystifying book Blockchain Basics: A Non-Technical Introduction in 25 Steps.
Every transaction recorded within a block has a unique hash value. Each block also contains a ‘header’ that includes a ‘root value’. This is a hash value of all the transactions recorded within it, as well as a hash value of the preceding block to determine the order of the blockchain (obviously, this does not apply to the very first block in the blockchain).
Figure 1. Examples of hash values that can be obtained from different hash functions applied to a message.
What does this all mean in terms of security? Because each hash value is unique to the item of data it represents, any attempt to change transaction data within a block would also change the hash value for that transaction. This would break the link with the unique root value in the block header and invalidate the entire data structure. For example, suppose the root value itself is changed: this then invalidates the link with the following block. It is not necessary for users to examine the actual data content to notice if it has been tampered with. The system detects the broken connections between hash values which indicate tampering (or possibly a technical fault). Tampering becomes all but impossible, as a hacker would need to alter the previously-recorded hash values all along the chain leading back to the target transaction, and to do this on every user’s ledger simultaneously.
Cryptographic keys to authorise messages
When a transaction is sent in a blockchain, how can you be sure that it really came from the person who appears to be the sender? The solution to this problem lies with the use of public and private cryptographic keys, and a digital signature scheme.
The sender of a message creates a hash value of the transaction, then signs the hash value using their private key and a signature algorithm. The recipient has access to both the transaction and the digital signature, and can use the sender’s public key and the hash value of the transaction to validate the transaction against the signature. The verification algorithm will only return true if the signature and transaction hash value are exactly the same as the sender’s, confirming that they sent the transaction. If the algorithm returns false, it indicates that either the transaction data has been tampered with, or the signature has been forged.
How do blocks get added?
A system of costs, rewards and punishments are used to maximise the likelihood that only valid blocks of transactions are added to the blockchain network. When a node creates new transaction data, these are distributed to every other node in the blockchain network. These nodes then scrutinize the transactions. Once satisfied that the transactions are valid, each node begins compiling the data into a new block.
In the Proof-of-Work consensus mechanism: to create a new block, each node must solve a ‘hash puzzle’. This is a problem that can only be solved by ‘brute force’ (trial and error), hence is computationally expensive. This is the cost of submitting a new block. When a node has solved the puzzle, it sends the newly-created block to all other nodes. The other nodes then verify the solution of the hash puzzle and all the transaction data in the block. The first node to create a block that is accepted as valid by the other nodes receives a financial reward for doing so, and its block is added to the blockchain ledger held at each node. The size of the reward – in the form of cryptocurrency - is determined algorithmically by the blockchain.
If a new block is found to be invalid, it is discarded and the nodes in the network continue processing transaction data or with finishing the hash puzzle of the new block. The node that submitted the invalid block is not rewarded.
In the event that a block is accepted but later found to be invalid, then that block and all subsequent blocks are marked as ‘invalid’ and treated as though they had been removed from the system. The submitting node loses its reward . All transactions that had been previously distributed and added in subsequent blocks are now added to users’ inboxes again for further processing.
The Proof-of-Work consensus mechanism is what Bitcoin uses, but this is not the only such mechanism. Other articles in this series provide information on some of the other available mechanisms.
Trust is not required
Because of these mechanisms, advocates for blockchain argue that transactions conducted via blockchain do not require participants to trust each other. There is another aspect of blockchain that makes it extremely difficult for dishonest parties to tamper with blocks that have already been added to the system: they would need to hack into the ledgers of every user simultaneously.
The next article: Joe Preece, of the University of Birmingham, will discuss blockchain’s potential use as a mechanism for rail ticketing.